Question
1 ) Write Short Notes on :
Answer :
1) Communication Protocol :
1 ) Write Short Notes on :
- Communication Protocol
- Structured Data Representation
- Scalable Connectivity
- Java Messaging Services
- Inter networking
Answer :
1) Communication Protocol :
- Communication protocols are formal descriptions of digital message formats and rules. They are required to exchange messages in or between computing systems and are required in telecommunications.
- Communications protocols cover authentication, error detection and correction, and signaling. They can also describe the syntax, semantics, and synchronization of analog and digital communications. Communications protocols are implemented in hardware and software. There are thousands of communications protocols that are used everywhere in analog and digital communications. Computer networks cannot exist without them.
Communications devices have to agree on many physical aspects of the data to be exchanged before successful transmission can take place. Rules defining transmissions are called protocols.
- There are many properties of a transmission that a protocol can define. Common ones include: packet size, transmission speed, error correction types, handshaking and synchronization techniques, address mapping, acknowledgement processes, flow control, packet sequence controls, routing, address formatting
- Popular protocols include: File Transfer Protocol (FTP), TCP/IP, User Datagram Protocol (UDP), Hypertext Transfer Protocol (HTTP), Post Office Protocol (POP3), Internet Message Access Protocol (IMAP), Simple Mail Transfer Protocol (SMTP).
2) Structured Data Representation
- Structured data refers to any data that resides in a fixed field within a record or file. This includes data contained in relational databases and spreadsheets
- Structured data is often managed using Structured Query Language (SQL) – a programming language created for managing and querying data in relational database management systems.
- Some formats used to represent structured data are:
i) JSON-LD
JavaScript notation embedded in a <script> tag in the page head or body. The markup is not interleaved with the user-visible text, which makes nested data items easier to express, such as the Country of a PostalAddress of a Music Venue of an Event. Also, Google can read JSON-LD data when it is dynamically injected into the page's contents, such as by JavaScript code or embedded widgets in your content management system.
ii) Microdata
An open-community HTML specification used to nest structured data within HTML content. Like RDFa, it uses HTML tag attributes to name the properties you want to expose as structured data. It is typically used in the page body, but can be used in the head.
iii) RDFa
An HTML5 extension that supports linked data by introducing HTML tag attributes that correspond to the user-visible content that you want to describe for search engines. RDFa is commonly used in both the head and body sections of the HTML page.
3) Scalable Connectivity
The Queue is responsible to hold the message until receiver is ready.
In PTP model, there is no timing dependency between sender and receiver.
In PTP model, there is timing dependency between publisher and subscriber.
3) Scalable Connectivity
- Scalability is an attribute that describes the ability of a process, network, software or organization to grow and manage increased demand.
- A system, business or software that is described as scalable has an advantage because it is more adaptable to the changing needs or demands of its users or clients.
- Scalability is often a sign of stability and competitiveness, as it means the network, system, software or organization is ready to handle the influx of demand, increased productivity, trends, changing needs and even presence or introduction of new competitors.
- To further understand scalability, here are two examples. First, a basic anti-virus program can become premium and be used by enterprises through downloading certain add-ons or paying for subscription. Because more resources may be added to it, it is considered scalable. On the other hand, more computers and servers can be added to a network in order to increase throughput or intensify security. This makes the network scalable.
4) Java Messaging Services (JMS)
- JMS (Java Message Service) is an API that provides the facility to create, send and read messages. It provides loosely coupled, reliable and asynchronous communication.
- JMS is also known as a messaging service.
- Messaging is a technique to communicate applications or software components.
- JMS is mainly used to send and receive message from one application to another.
Advantage of JMS
1) Asynchronous: To receive the message, client is not required to send request. Message will arrive automatically to the client.
2) Reliable: It provides assurance that message is delivered.
Messaging Domains
There are two types of messaging domains in JMS.
- Point-to-Point Messaging Domain
- Publisher/Subscriber Messaging Domain
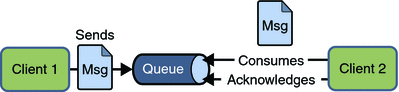
1) Point-to-Point (PTP) Messaging Domain
In PTP model, one message is delivered to one receiver only. Here, Queue is used as a message oriented middleware (MOM).The Queue is responsible to hold the message until receiver is ready.
In PTP model, there is no timing dependency between sender and receiver.

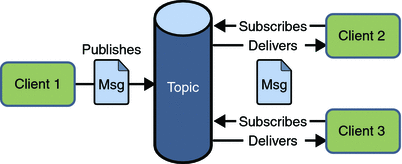
2) Publisher/Subscriber (Pub/Sub) Messaging Domain
In Pub/Sub model, one message is delivered to all the subscribers. It is like broadcasting. Here, Topic is used as a message oriented middleware that is responsible to hold and deliver messages.In PTP model, there is timing dependency between publisher and subscriber.

5) Inter networking
- Internetworking is the process or technique of connecting different networks by using intermediary devices such as routers or gateway devices.
- Internetworking ensures data communication among networks owned and operated by different entities using a common data communication and the Internet Routing Protocol. The Internet is the largest pool of networks geographically located throughout the world but these networks are interconnected using the same protocol stack, TCP/IP. Internetworking is only possible when the all the connected networks use the same protocol stack or communication methodologies.
- Internetworking is also implemented using internetworking devices such as routers.These are physical hardware devices which have the ability to connect different networks and ensure error free data communication. They are the core devices enabling internetworking and are the backbone behind the Internet.
2 ) Documentation of Application Architecture and it's Design Strategies
- The architecture of an enterprise application is documented in the System Architecture Document (SAD).
- The term high level design is also used interchangeably with SAD.
- It acts as a blueprint for the detailed design process.
- The detailed design of an enterprise application can be documented in several ways - technical layer wise, module/use case wise, component wise, or typically a mix of them.
- The overall objective of the design documentation is effective communication among application teams which are involved in design, development and deployment activities.
- The design documentation should include, for each use case, the presentation, business and data access components.
- In addition to this, integration and database designs may be documented separately.
-Applications architecture strategy involves ensuring the applications and the integrations align with the growth strategy of the organization. If an organization is a manufacturing organization with fast growth plans through acquisitions, the applications architecture should be nimble enough to encompass inherited legacy systems as well as other large competing systems.
No comments:
Post a Comment